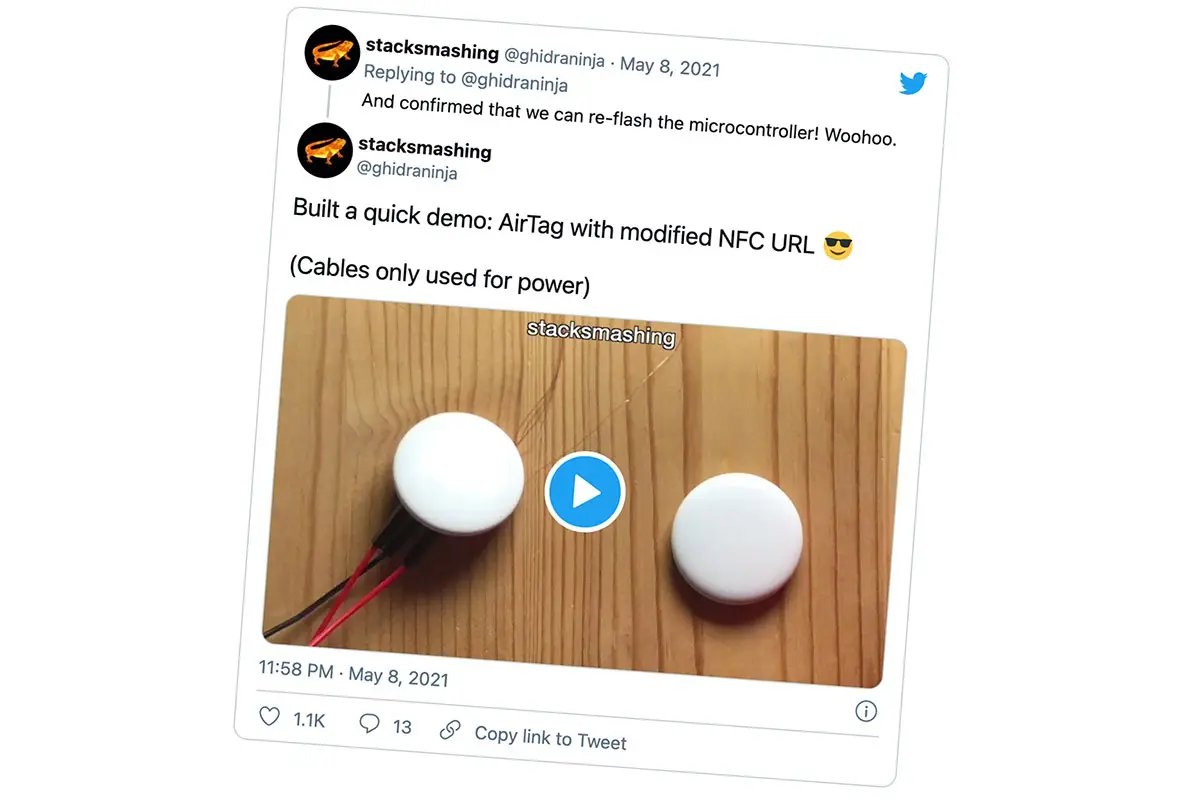
A hacker has reprogrammed the microcontroller in one of Apple’s new AirTag location tracking devices to make the NFC tag within it point to an arbitrary URL.
The way in which the hack has been performed indicates that the NFC portion of an AirTag is not a static tag, but rather a dynamic one that can be changed from the product’s microcontroller.
AirTags usually direct NFC devices that scan them to open the ‘found.apple.com’ website, but in this instance a German security researcher known as Stack Smashing changed the tag to point at their own website instead by re-flashing the microcontroller.
A tweet announcing the development includes a video showing a modified AirTag NFC read in action.
Apple launched its much-anticipated UWB-based AirTag item trackers in April 2021.
Next: Visit the NFCW Expo to find new suppliers and solutions